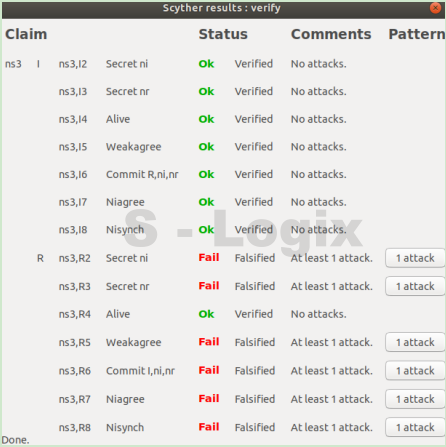
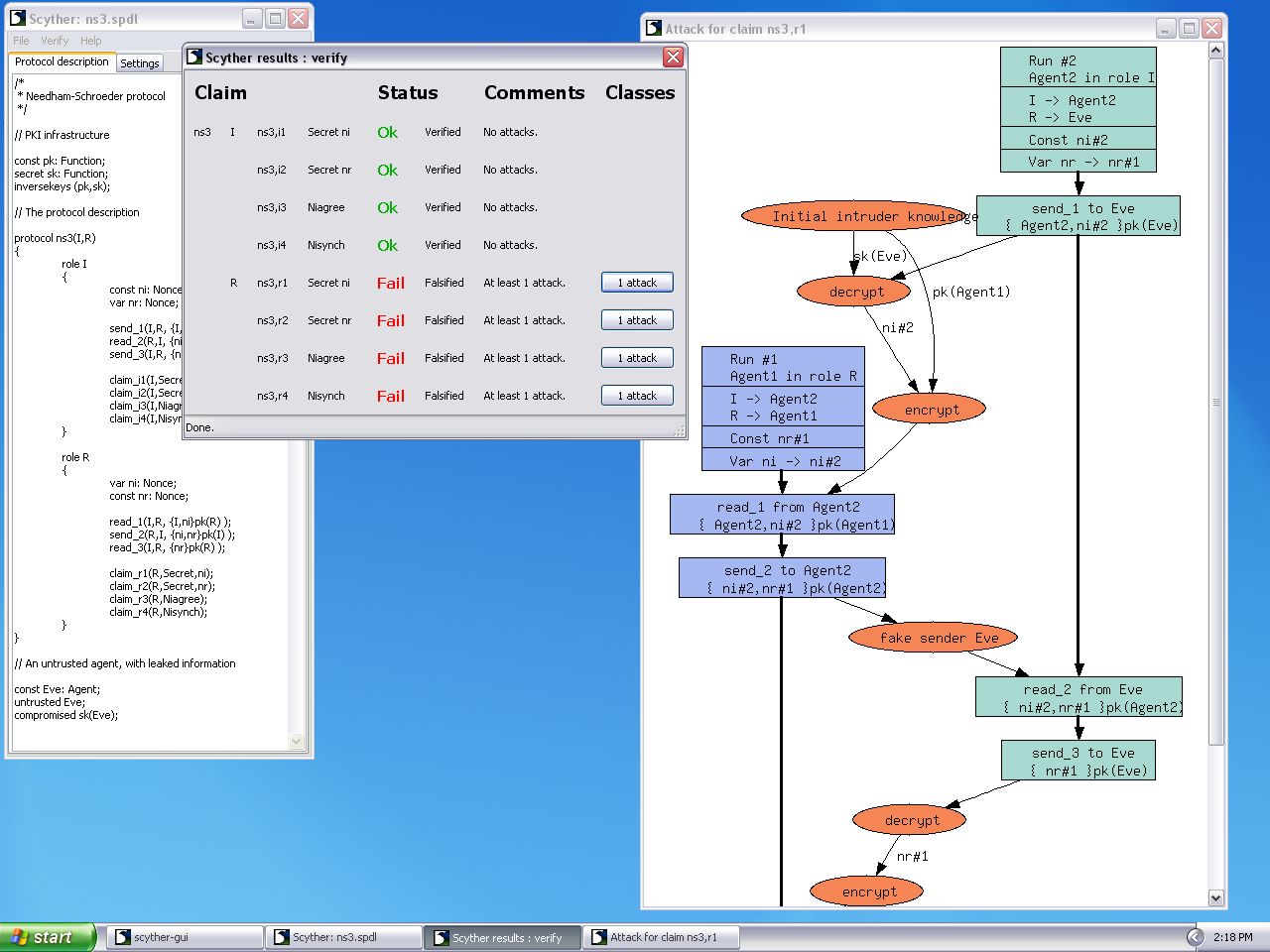
GitHub - binhnguyen1984/scyther-abstraction: The Scyther-abstraction Tool for the symbolic analysis of security protocols

PDF) Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Hazem A . Elbaz - Academia.edu